There’s been a deluge of a fake copyright infringement notice circulating the website owners claiming to be from disgruntled graphic designers that may have found its way into your inbox. If you fall prey to this scam, it could result in your computer being infected with spyware or worse, ransomware.
So unless you receive a certified letter from the law firm Dewey, Cheatem, & Howe regarding a website copyright infringement notice, it’s a phishing scam. Whatever you do, do not click on the link!
What is a Phishing Scam?
Phishing is a cybercrime in which scammers try to lure sensitive information or data from you, by disguising themselves as a trustworthy source. Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message.
With that said, we decided to do something about it.
WEBPRO provides an added layer of defense for our clients when it comes to phishing attempts. We call it the Phish Finder Pro. I know but we had to call it something! The very thought you or an employee could be one click away from losing your company to an unaffordable ransomware situation is enough to make Buddha a chain-smoker.
We’ve all become dangerously dependent on reading emails from our smartphones. Why is it so dangerous? It’s dangerous because it’s very difficult to know the real thing from a fake-a-roo or spoof attempt, especially if you don’t know how to read the email header information. Since 97% don’t or won’t bother to check, we’re here to warn everyone that your smartphone although convenient, can be your biggest liability if you are not extra careful.
Phishing scams could care less what brand smartphone you purchased or what carrier you use. Falling prey to an innocent looking email request form coming from your website on your new $1299.00 iPhone can be the mother of all bear traps if you don’t know what you’re really looking at or haven’t the talent to stop phishing web form attacks.
Speaking of bears, below is an example of a blocked phishing form that was prevented from entering a client’s inbox below.
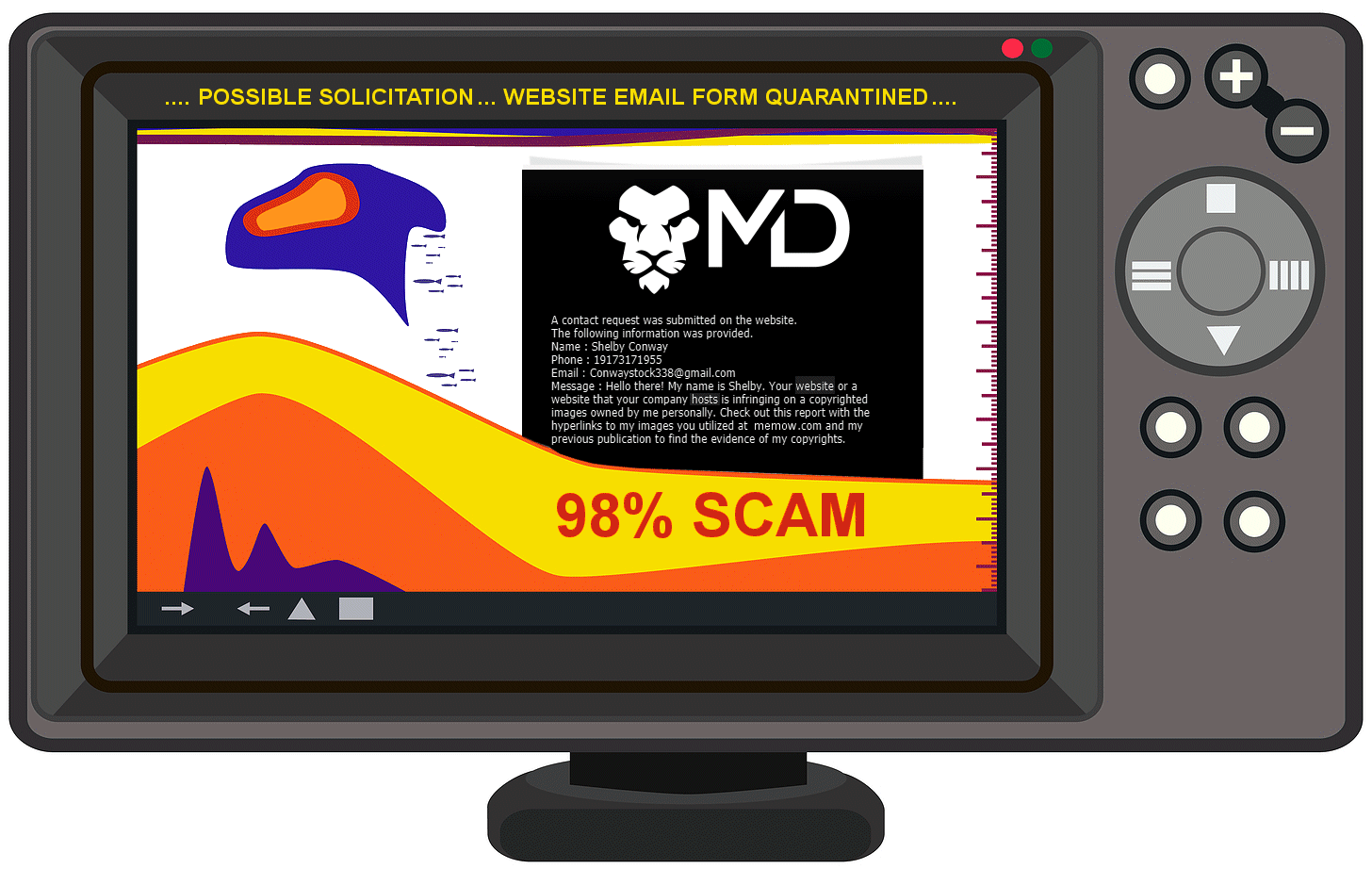
I’ll tell you how we quarantine these attacks in a second but let these statistics sink in.
• Email delivers malware and ransomware over 95% of the time
• Phishing is responsible for more than 83%
• Over $18,000 is lost every minute due to phishing attacks
• 60 % of breaches involved vulnerabilities for which a patch was available but not applied either from your smartphone, WordPress or an email client like Microsoft’s Office365 which recently had the biggest breech in history. And that vulnerability was widely known by Microsoft (who did nothing about until they had to) left the problem child in plain sight for over a decade.
Symantec commented almost one in every 2,000 emails is phishing related which basically equates to 135 million phishing attacks every day. The last thing you need to be worried about is vetting a potential lead from your website.
Since creating our little free of charge anti-phishing charter service for our clients, we’ve managed to block over 16,400 attempts – and that’s with false pos+ rate less than 1.2% in 3 years. Any malicious or nefarious phishing attempts are clearly labeled as a “Possible Solicitation” in the subject line. In the event of a false positive, our clients are still able to double check all inbound leads in their lead container.

Block and Tackle SPAM
In addition to quarantining phishing attempts, the Phish Finder doubles as a spam block and tackle utility by eliminating those nasty and irritating spammers who abuse your web forms. Why anyone would knowingly trespass could ever hope to curry your business let alone be welcomed after violating your web form which is intended for legitimate business is beyond me. It is because of these cyber-jerks we were so motivated to build this time-saving service for our clients.
Below is a spam example. This one came from Your Secret Weapon. Unfortunately, spam and phishing is a constant but that's OKAY, we have have our own secret weapon too.

That’s how we do it.
Plato was right. Necessity is the mother of invention. WEBPRO saw a crack and simply filled it the best we knew how. If you don’t have someone thinking out the box and watching your six, it’ll be a matter of time before you’re nailed because the bad guys are betting, they’ll eventually catch you off guard.
A special thanks goes to Charlie and Tripp for designing and developing the Phish Finder Pro for our clients. We really hit a home run with this one!
